Which of the Following Is the Best Definition for Non-repudiation
Subnetting is used to split a network into smaller portions. Nonrepudiation is a method of guaranteeing message transmission between parties via digital signature andor encryption.

It Security Policy Key Components Best Practices For Every Business Bmc Software Blogs
First week only 499.
. NS4009 Technical non-repudiation refers to the assurance a Relying Party has that if a public key is used to validate a digital signature that signature had to have. Non-Repudiation A sender cannot deny sending a message which has a digital signature. Non-repudiation means putting measures in place that will prevent one party from denying they received or agreed to a transaction.
The term is often seen in a legal setting when the authenticity of a signature is being challenged. Which of the following is the best definition for non-repudiation. None Repudiation refers to having proof of any transaction made from the requester to the authoriser and also from the authoriser to the requester.
Non-repudiation refers to a situation where a statements author cannot successfully dispute its authorship or the validity of an associated contract. What is the acronym of URL. The other four pillars are.
Which of the following is the best definition for war-driving. Which of the following aspects of PKI BEST ensures the identity of the sender. Solution for What is the definition of the Principle of Non-Repudiation.
Fill in the following table showing the results of the indicated instructions. Assurance that the sender of information is provided with proof of delivery and the recipient is provided with proof of the senders identity so neither can later deny having processed the information. After undergoing several audits the owner determined that current levels of non-repudiation were insufficient.
I will try my best to answer this question. Those who exploit systems for harm such as to erase files change data or deface Web sites are typically called. This is an electronical proof that will have information of the person who made any transaction.
It has its roots in legal processes intended to prevent entities from claiming they didnt agree to something or sign a document. It is one of the five pillars of information assurance IA. The other four are availability integrity confidentiality and authentication.
Nonrepudiation is often used for digital contracts signatures and email messages. Processes that verify which user performs what action. Nonrepudiation is one of the five pillars of information assurance IA which is the practice of managing information-related risks and protecting information systems like computers servers and enterprise networks.
Which of the following is designed to stop an intrusion on a specific server. A Keyed-Hash Message. The process to Verify Which user performs the action.
According to the Information Technology Act 2000 digital signatures mean authentication of any electronic record by a subscriber by means of an electronic method or procedure in accordance with the provisions of section 3. It is another term for user authentication. The sender is really the one who claims to be the sender of the.
Begingroup Actually non-repudiation is not matched by identity binding at all. CLICK TO SKIP AD AND GET ANSWER. Class A IPs with range 0-126 are reserved for multicasting.
This explanation above will help you implement some best practices of Security Information in your systems using. In such an instance the authenticity is being repudiated. Processes that verify which user performs what action.
CLICK TO SKIP AD AND GET ANSWER. Non-repudiation is the ability to prove or disprove that something happened such as a financial transaction or a binding signature on a legal agreement. Start your trial now.
The process to Verify Which user performs the action. Class A IPs with range 0-126 are reserved for multicasting. Subnetting is used to split a network into smaller portions.
If the recipient. John Spacey December 21 2016. Digital documents are ubiquitous.
Further the IT Act 2000 deals. Jane a security administrator has observed repeated attempts to break into a server. The systems attractiveness the information contained on the system and how much traffic.
What is the acronym of URL. Having received a document we want to make sure that. Which of the following is the best definition for non-repudiation.
Which of the following is the best definition for non-repudiation. Which of the following is the best definition for non-repudiation. The main idea is that you have a transferable proof that the owner of a private key authored a message.
Non-repudiation is a much desired property in the digital world. Assurance that the sender is provided with proof of delivery and that the recipient is provided with proof of the senders identity so that neither can later deny having processed the data. This article describes that property and shows how it can be achieved by using digital signatures.
An information system owner has supplied a new requirement to the development team that calls for increased non-repudiation within the application. Which of the following types of privacy laws affect computer security. Processes that verify which user performs what action.
Sure this somewhat binds it to a public key but not to an arbitrary identity yet. Which of the following is the best definition for non-repudiation. For example Mallory buys a cell phone for 100 writes a paper cheque as.

Solved 1 Which Of The Following Can Be Used To Mitigate Chegg Com

Itil Service Strategy Overview Critical Success Factors Strategies Portfolio Management

Itil Information Security Management Security Management Access Control

What Is Nonrepudiation Definition From Techopedia
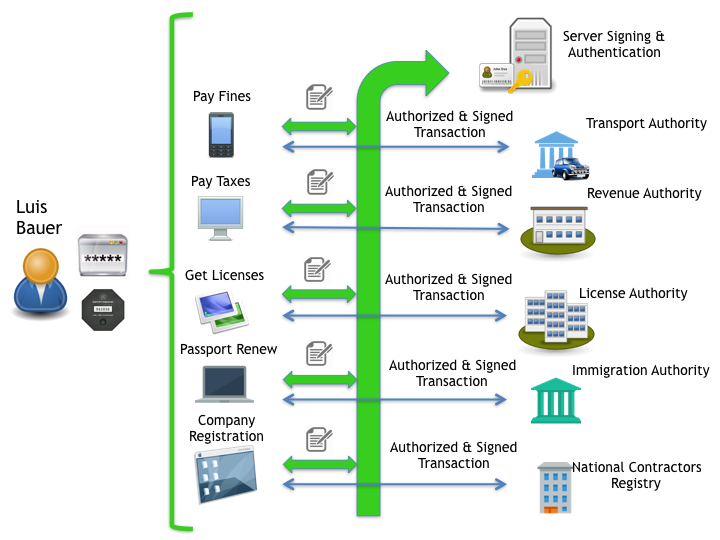
Centralized Authentication And Signing For E Government

Quiz Worksheet Non Repudiation In Network Security Study Com

What Is Non Repudiation In Network Security Study Com

Service Catalogue Management Change Management Portfolio Management Data Services

Itil Service Strategy Overview Critical Success Factors Portfolio Management Relationship Management

A Bitcoin Digital Signature And Its Verification Are One Of The Main Key Secrets Behind The Bitcoin Protocol It Allows Non Rep Buy Bitcoin Bitcoin Free Advice

Network Security Services Msa Technosoft Network Security Tech Blogs Security Service

Reddit Cissp Cissp Cheat Sheets Cybersecurity Infographic Cyber Security Education Cheat Sheets

Release Deployment Management Management Data Architecture Deployment

Held Once A Year Program On Cyber Security Studies Focuses On Strategic Objectives Techniques Policies And Best Practices That Secure And Defend The Availability Integrity Authentication Confidentiality And Non Repudiation Of Information And

Build In 7 Security Layers To Make Exchange Secure And Reliable Bitroyal Exchange Supports A Wide Range Of Cryptocurrency Buy Bitcoin Bitcoin Cryptocurrency

Itil Information Security Management Risk Analysis Internal Audit Self Assessment
Comments
Post a Comment